SSM supports the following registries:
- ACR (Azure Container Registry)
- CUSTOM (Self-hosted Registry)
- ECR (Amazon Elastic Container Registry)
- GCR (Google Container Registry)
- GHCR (GitHub Container Registry)
- GITLAB (GitLab Container Registry)
- HUB (Docker Hub)
- LSCR (LinuxServer Container Registry)
- Quay
ℹ️ Default registries
By default, the following registries will be available using anonymous access: ECR, GHCR, GCR, HUB, QUAY
Configuring a registry
1. Go to settings, "Registries" tab

2. Select a predefined integration or custom integration (see below)
ACR (Azure Container Registry)
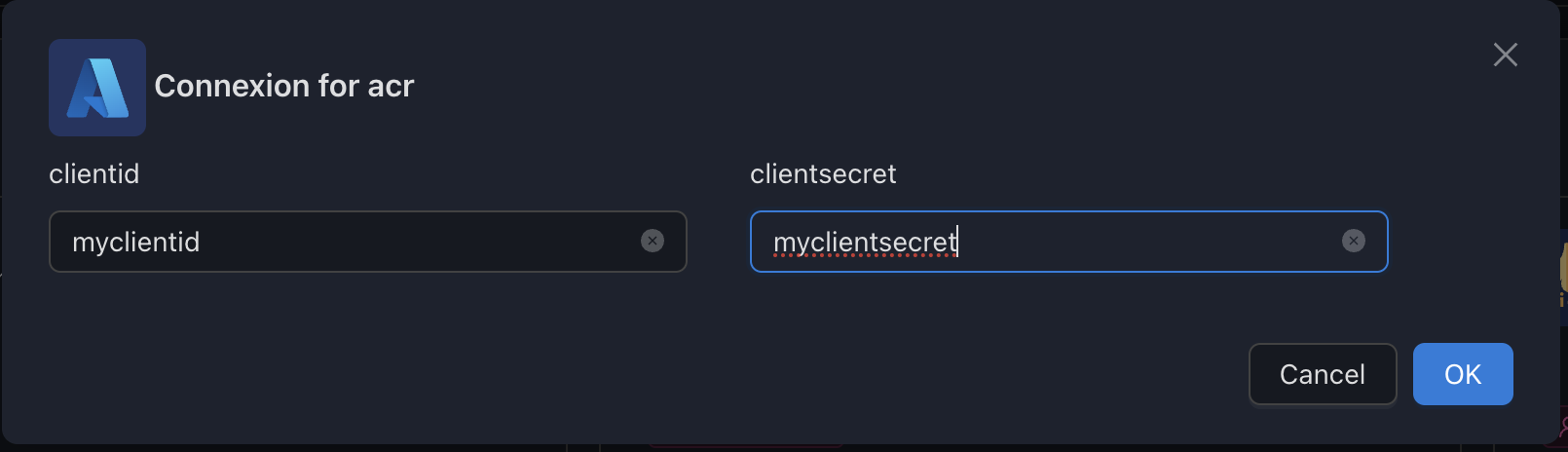
The acr registry lets you configure ACR integration.
Variables
| Name | Required | Description | Supported values | Default value when missing |
|---|---|---|---|---|
clientid | 🔴 | Service Principal Client ID | See Service Principal Auth | |
clientsecret | 🔴 | Service Principal Secret | See Service Principal Auth |
Example
How to create Registry credentials on Microsoft Azure Platform
Create a Service Principal
Follow the official Azure documentation.
Get the Client Id and the Client Secret of the created Service Principal
Go to your Container Registry and click on the Access Control (IAM) Menu
Click to Add a role assignment
Select the AcrPull role and assign it to your Service Principal 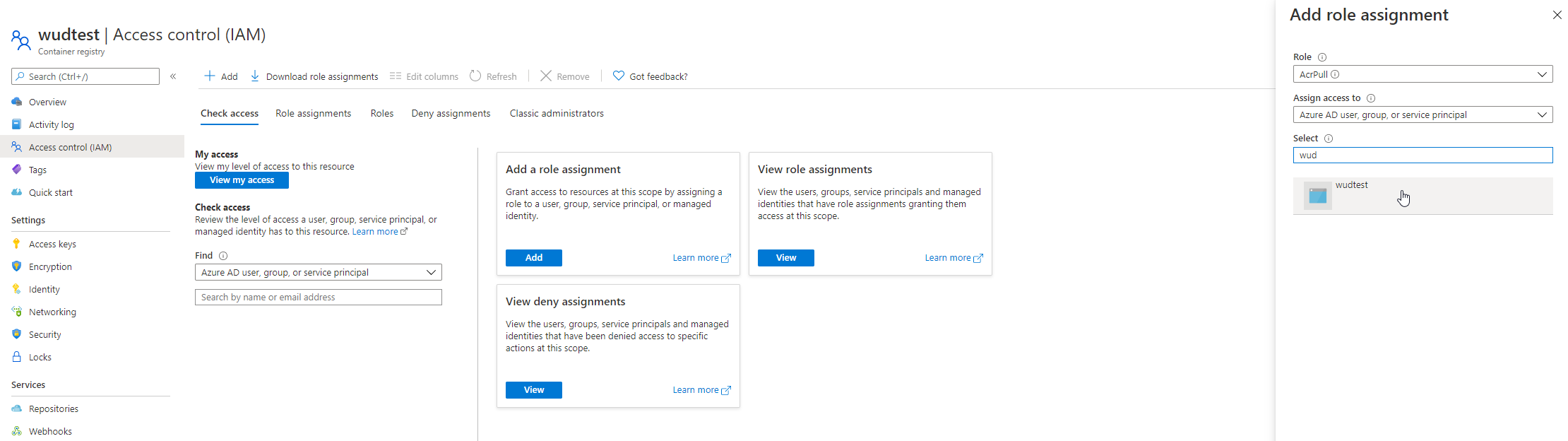
CUSTOM (Self-hosted Docker Registry)
The custom registry lets you configure a self-hosted Docker Registry integration.
Variables
| Env var | Required | Description | Supported values | Default value when missing |
|---|---|---|---|---|
url | 🔴 | Registry URL (e.g. http://localhost:5000) | ||
login | ⚪ | Login (when htpasswd auth is enabled on the registry) | password must be defined | |
password | ⚪ | Password (when htpasswd auth is enabled on the registry) | login must be defined | |
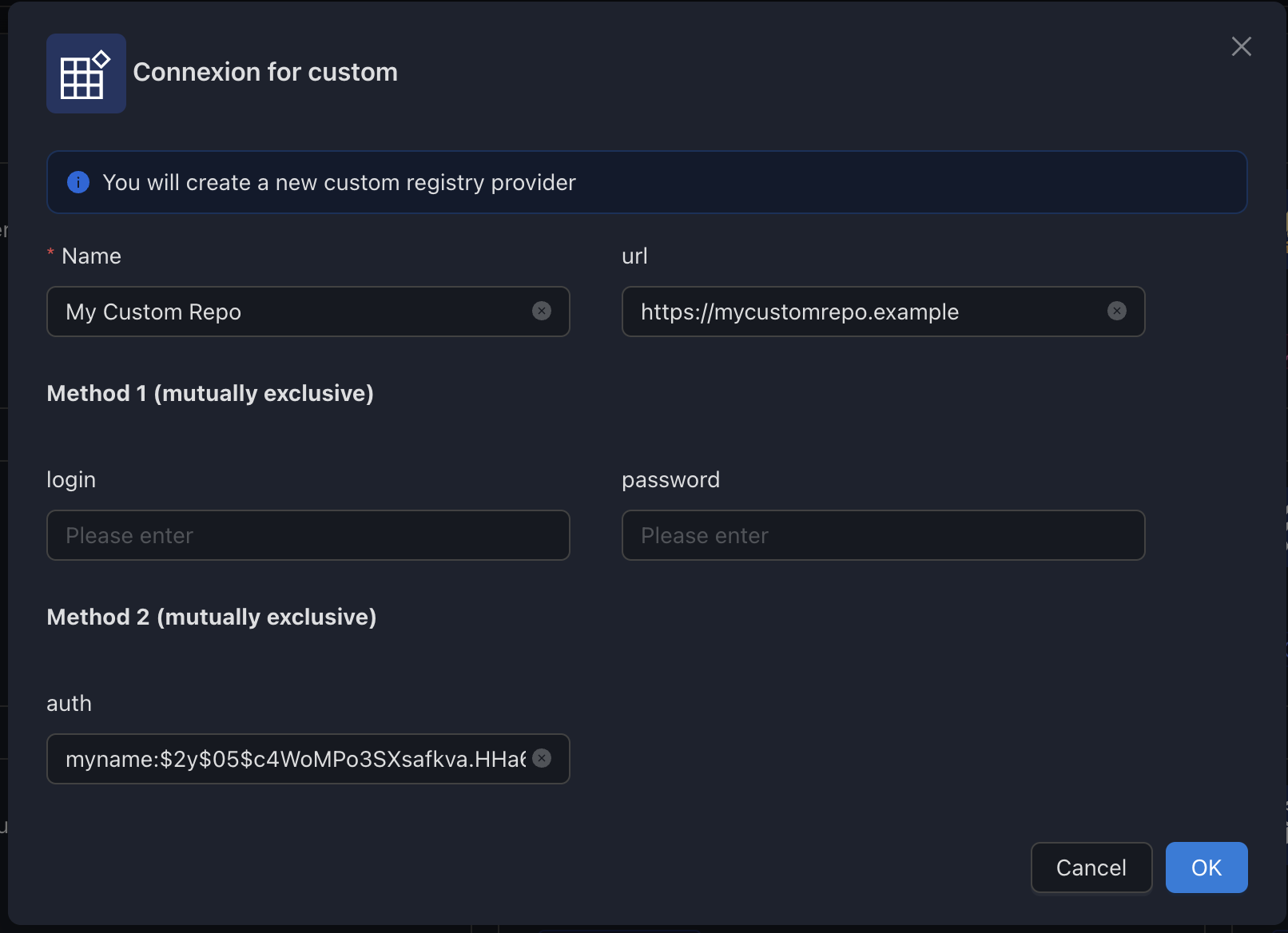
auth | ⚪ | Htpasswd string (when htpasswd auth is enabled on the registry) | login/password must not be defined |
Examples
Configure for anonymous access
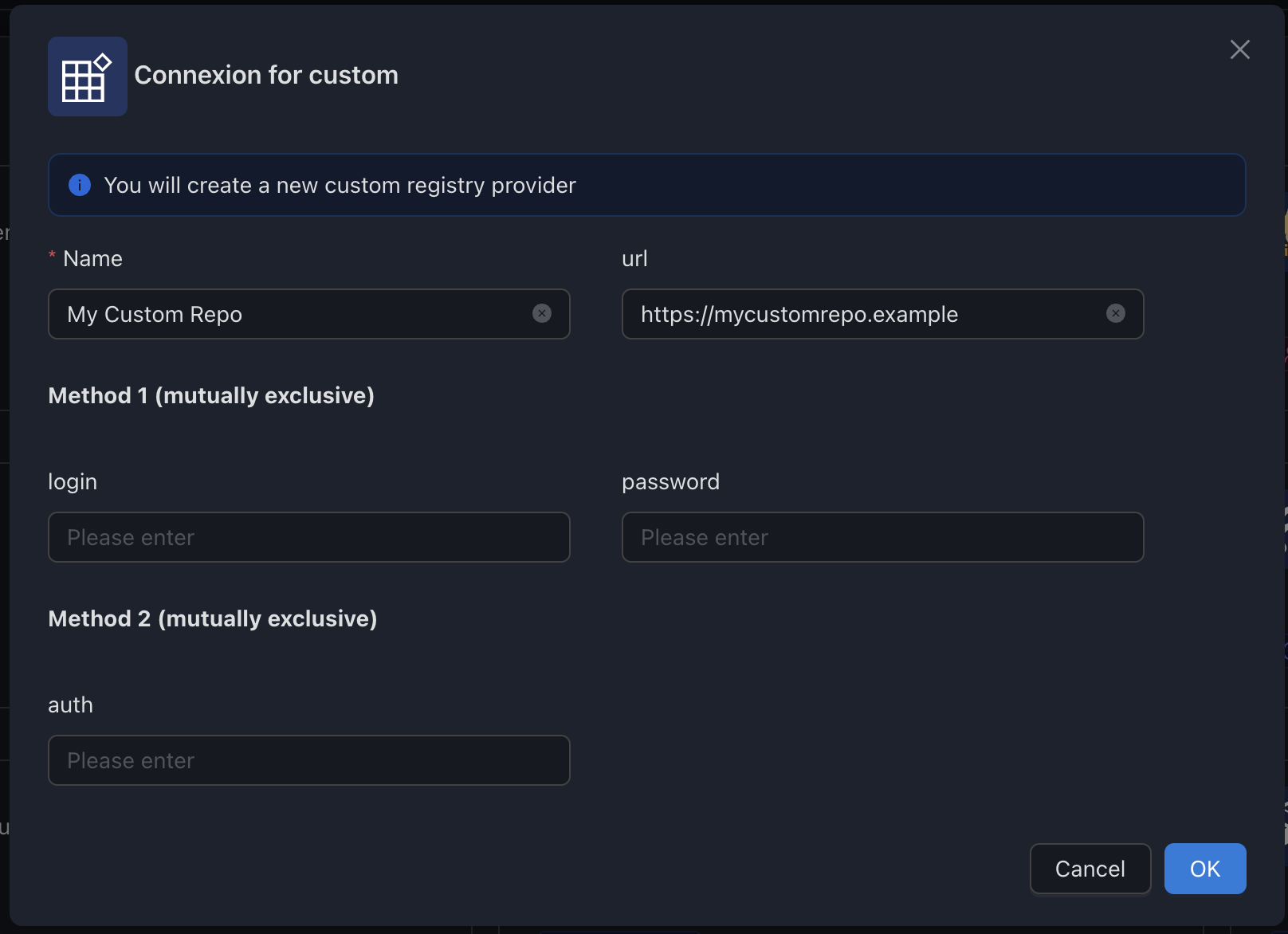
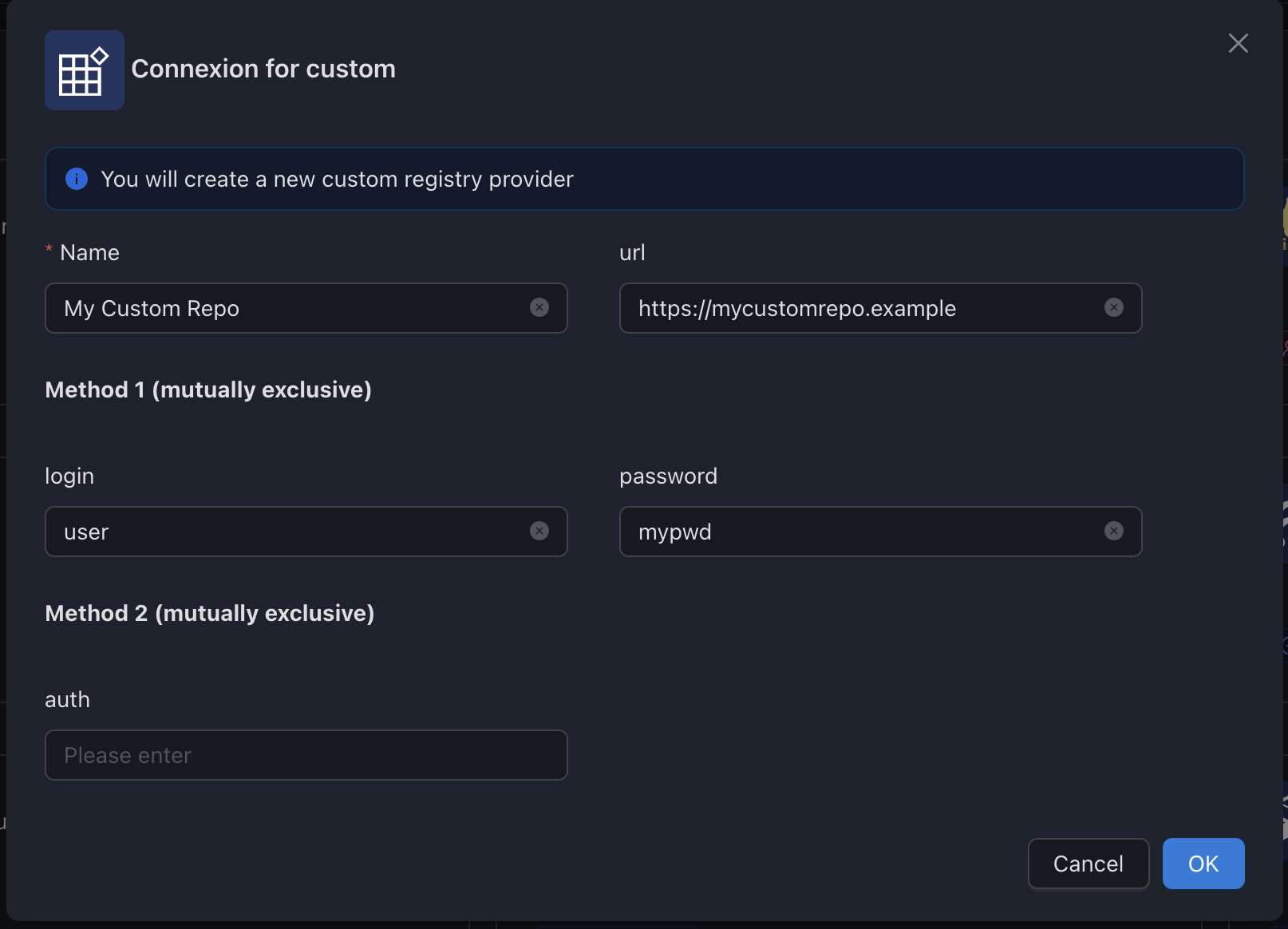
Configure for Basic Auth
ECR (Amazon Elastic Container Registry)
The ecr registry lets you configure ECR integration.
Variables
| Env var | Required | Description | Supported values | Default value when missing |
|---|---|---|---|---|
region | 🔴 | A valid AWS Region Code | AWS Region list | |
accesskey | 🔴 | A valid AWS Access Key Id | Standard AWS Credentials | |
secretaccesskey | 🔴 | A valid AWS Secret Access Key | Standard AWS Credentials |
!> The AmazonEC2ContainerRegistryReadOnly Policy (or higher) must be attached to the AWS IAM User.
Examples
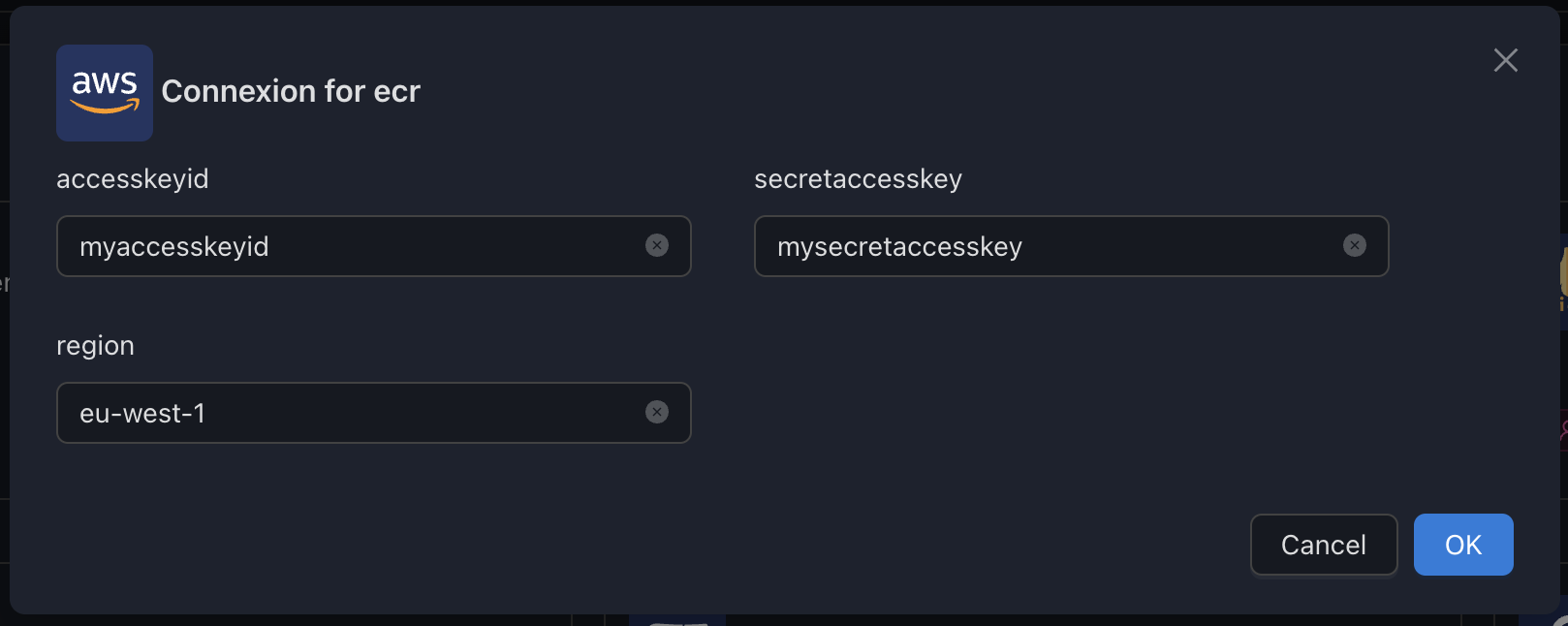
How to create an AWS IAM user and get programmatic access
1. Login to your Go to the IAM Service from your AWS Console and create a new user

2. Attach the AmazonEC2ContainerRegistryReadOnly policy to the user
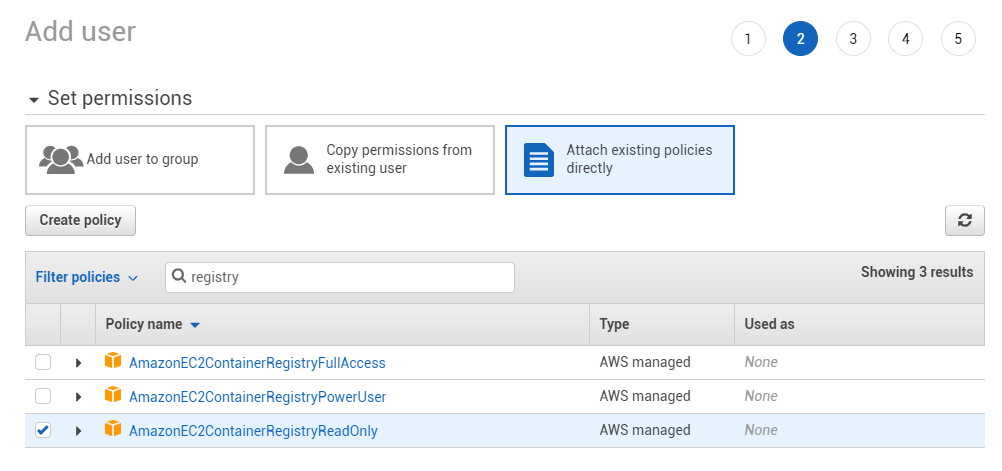
3. Get your AccessKeyId and your Secret Access Key and configure SSM with them

FORGEJO
The forgejo registry lets you configure a self-hosted Forgejo integration.
Variables
| Env var | Required | Description | Supported values | Default value when missing |
|---|---|---|---|---|
url | 🔴 | Registry URL (e.g. https://forgejo.acme.com) | ||
login | 🔴 | Gitea username | password must be defined | |
password | 🔴 | Gitea password | login must be defined | |
auth | ⚪ | Htpasswd string (when htpasswd auth is enabled on the registry) | login/password must not be defined |
Examples
Configure


GCR (Google Container Registry)
The gcr registry lets you configure GCR integration.
Variables
| Env var | Required | Description | Supported values | Default value when missing |
|---|---|---|---|---|
clientemail | ⚪ | Service Account Client Email (required for private images access) | See Service Account credentials | |
privatekey | ⚪ | Service Account Private Key (required for private images access) | See Service Account credentials |
Examples
Configure for authenticated access
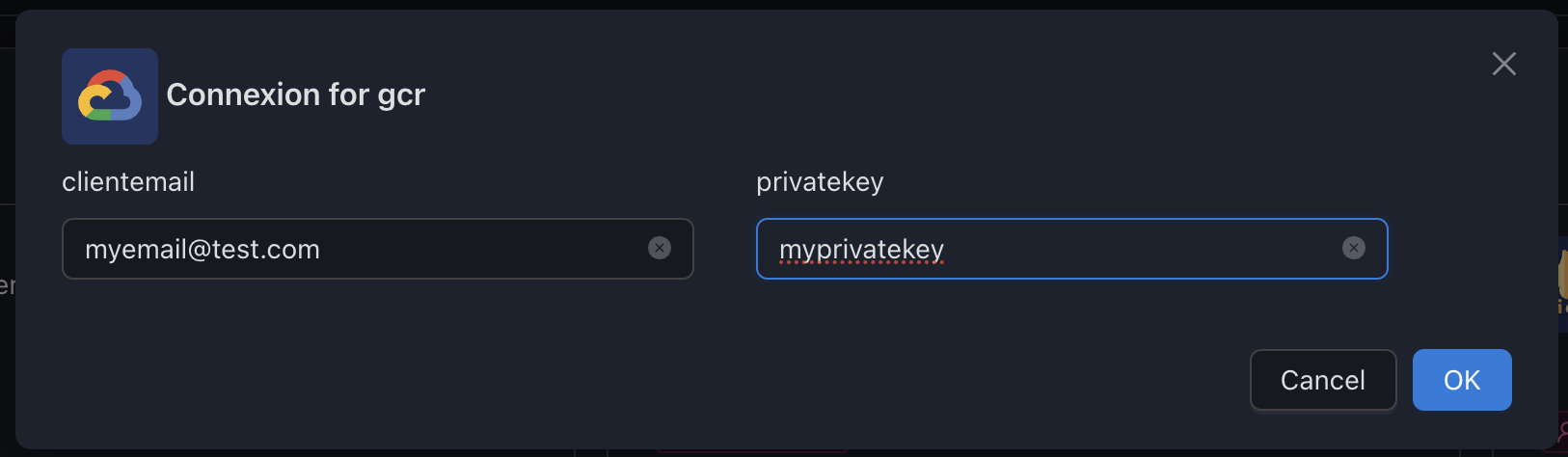
How to create a Service Account on Google Cloud Platform
1. Go to the Service Account page
2. Create a new Service Account
3. Add the Container Registry Service Role
4. Save the Service Account
5. Create a new key for the newly created Service Account
6. Download the keyfile JSON file and store it securely
7. Open the JSON file, get the client_email and private_key values and configure SSM with them
GHCR (GitHub Container Registry)
The ghcr registry lets you configure GHCR integration.
Variables
| Env var | Required | Description | Supported values | Default value when missing |
|---|---|---|---|---|
username | ⚪ | GitHub username | ||
token | ⚪ | GitHub token | GitHub password or GitHub Personal Token |
Examples
Configure to access private images (credentials needed)
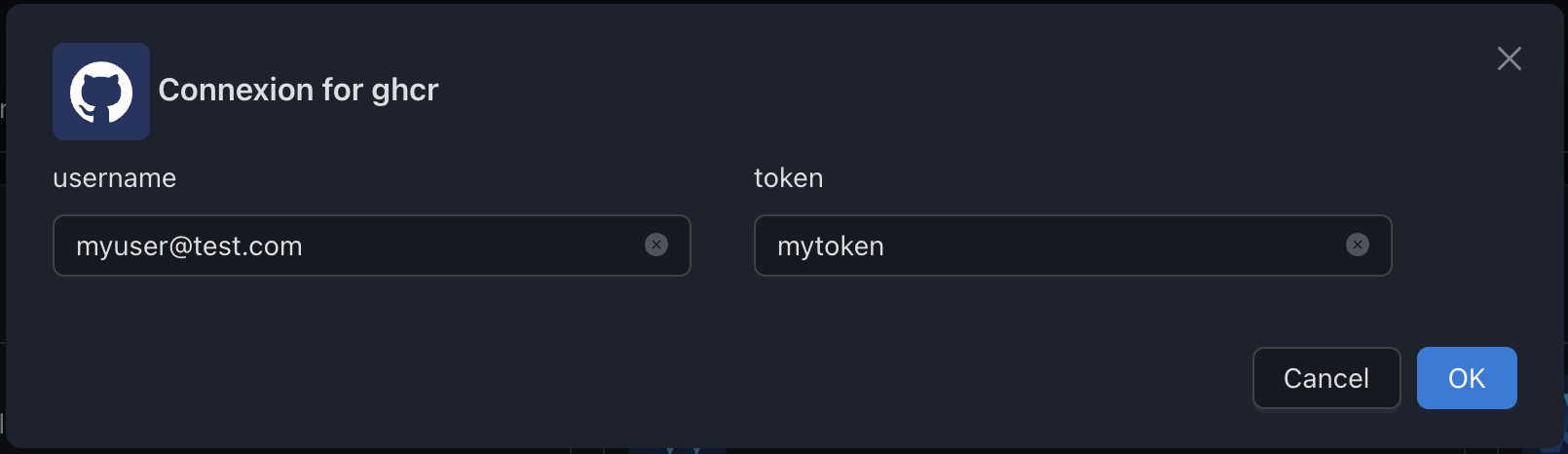
How to create a GitHub Personal Token
Go to your GitHub settings and open the Personal Access Token tab
Click on Generate new token
Choose an expiration time & appropriate scopes (read:packages is only needed for SSM) and generate. 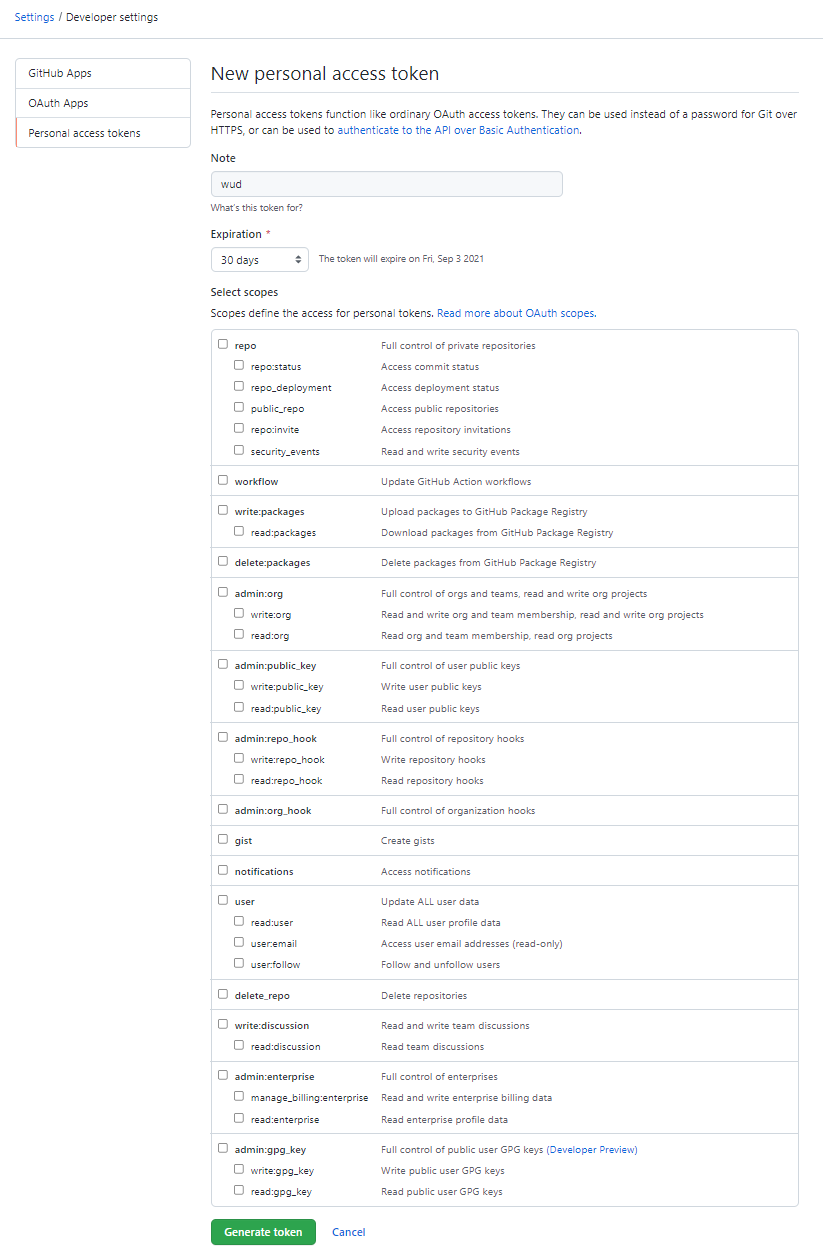
Copy the token & use it as the token value
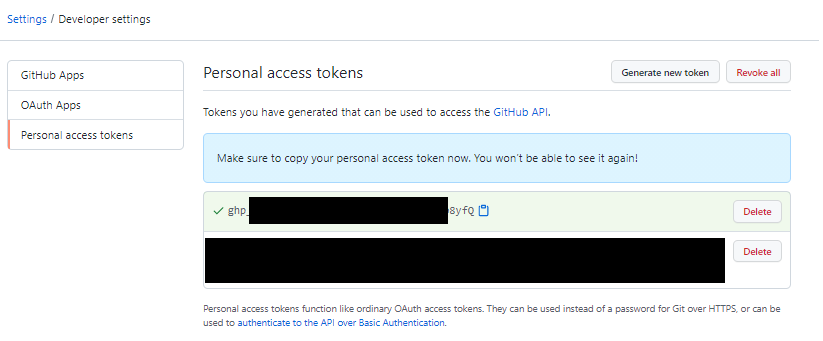
GITEA
The gitea registry lets you configure a self-hosted Gitea integration.
Variables
| Env var | Required | Description | Supported values | Default value when missing |
|---|---|---|---|---|
url | 🔴 | Registry URL (e.g. https://gitea.acme.com) | ||
login | 🔴 | Gitea username | password must be defined | |
password | 🔴 | Gitea password | login must be defined | |
auth | ⚪ | Htpasswd string (when htpasswd auth is enabled on the registry) | login/password must not be defined |
Examples
Configure
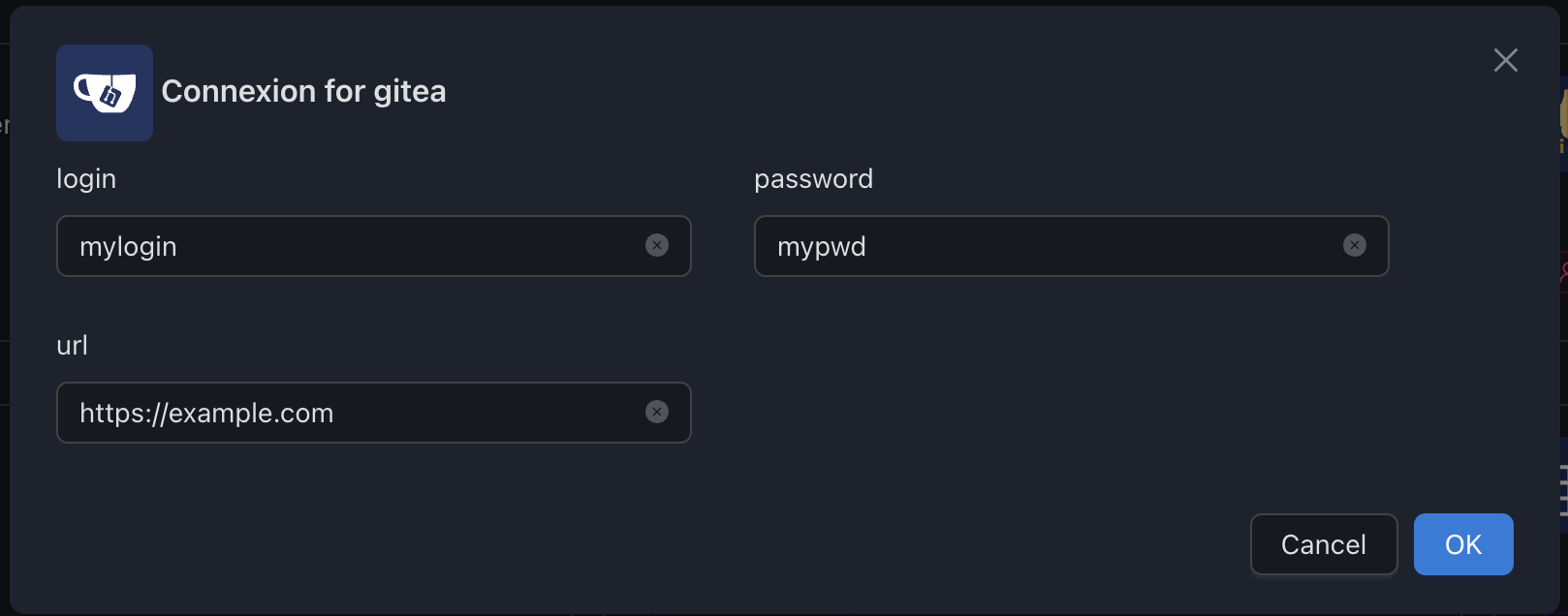
GitLab (GitLab Container Registry)
The gitlab registry lets you configure GitLab integration.
Variables
| Env var | Required | Description | Supported values | Default value when missing |
|---|---|---|---|---|
url | 🔴 | GitLab Registry base URL | https://registry.gitlab.com | |
authurl | 🔴 | GitLab Authentication base URL | https://gitlab.com | |
token | 🔴 | GitLab Personal Access Token |
Examples
Configure to access images from gitlab.com
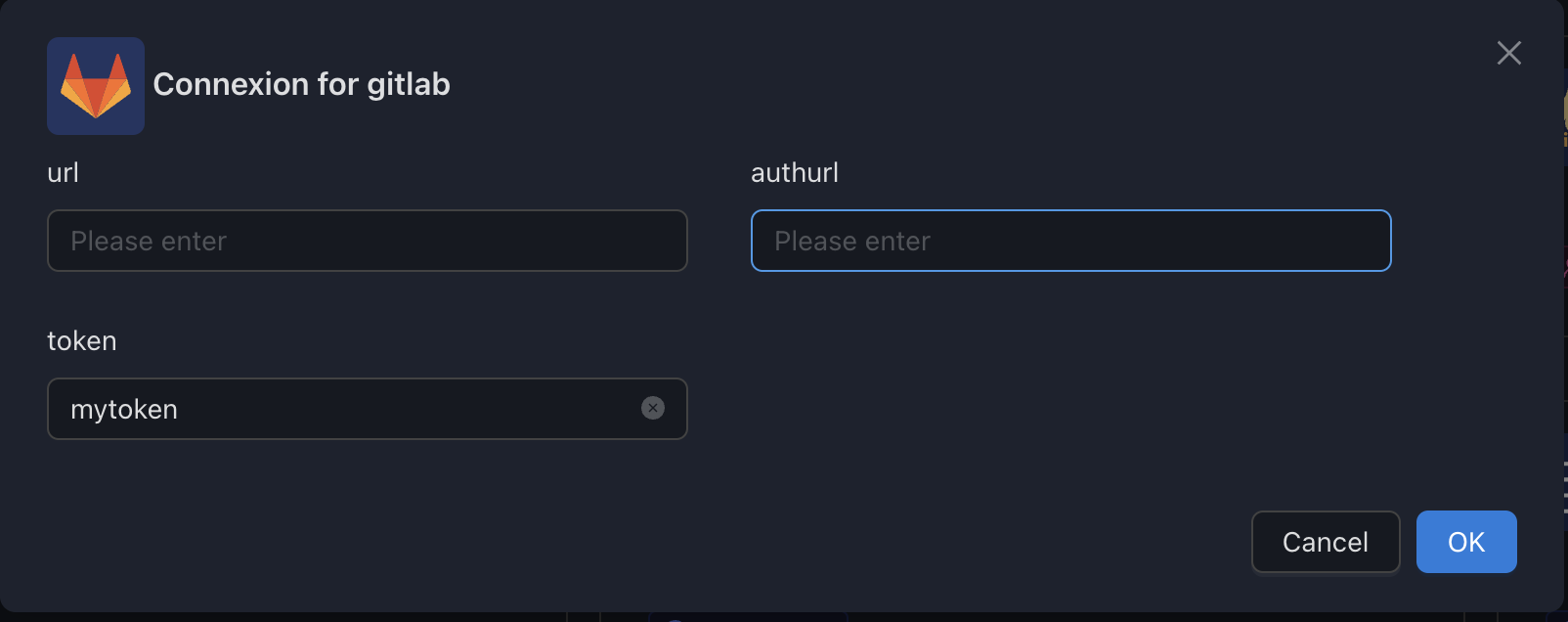
Configure to access images from self-hosted GitLab instance

How to create a GitLab Personal Access Token
Go to your GitLab settings and open the Personal Access Token page
Enter the details of the token to be created
Choose an expiration time & appropriate scopes (read_registry is only needed for SSM) and generate. 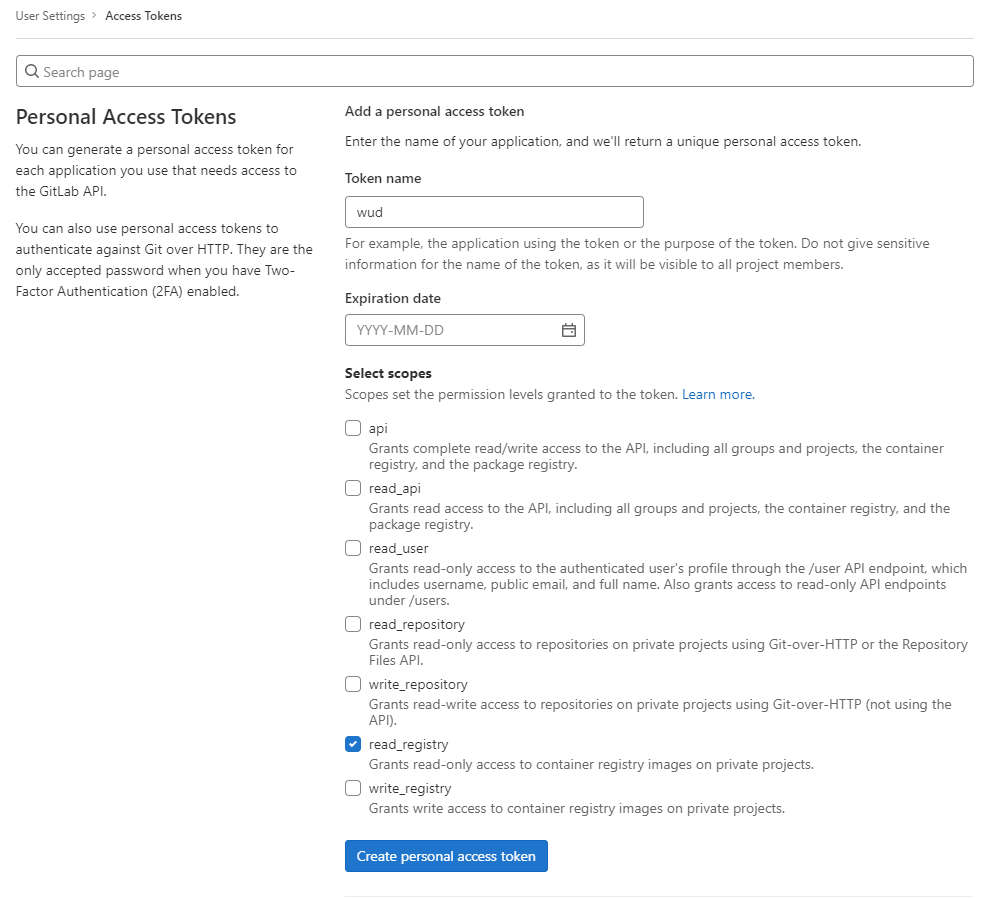
Copy the token & use it as the token value

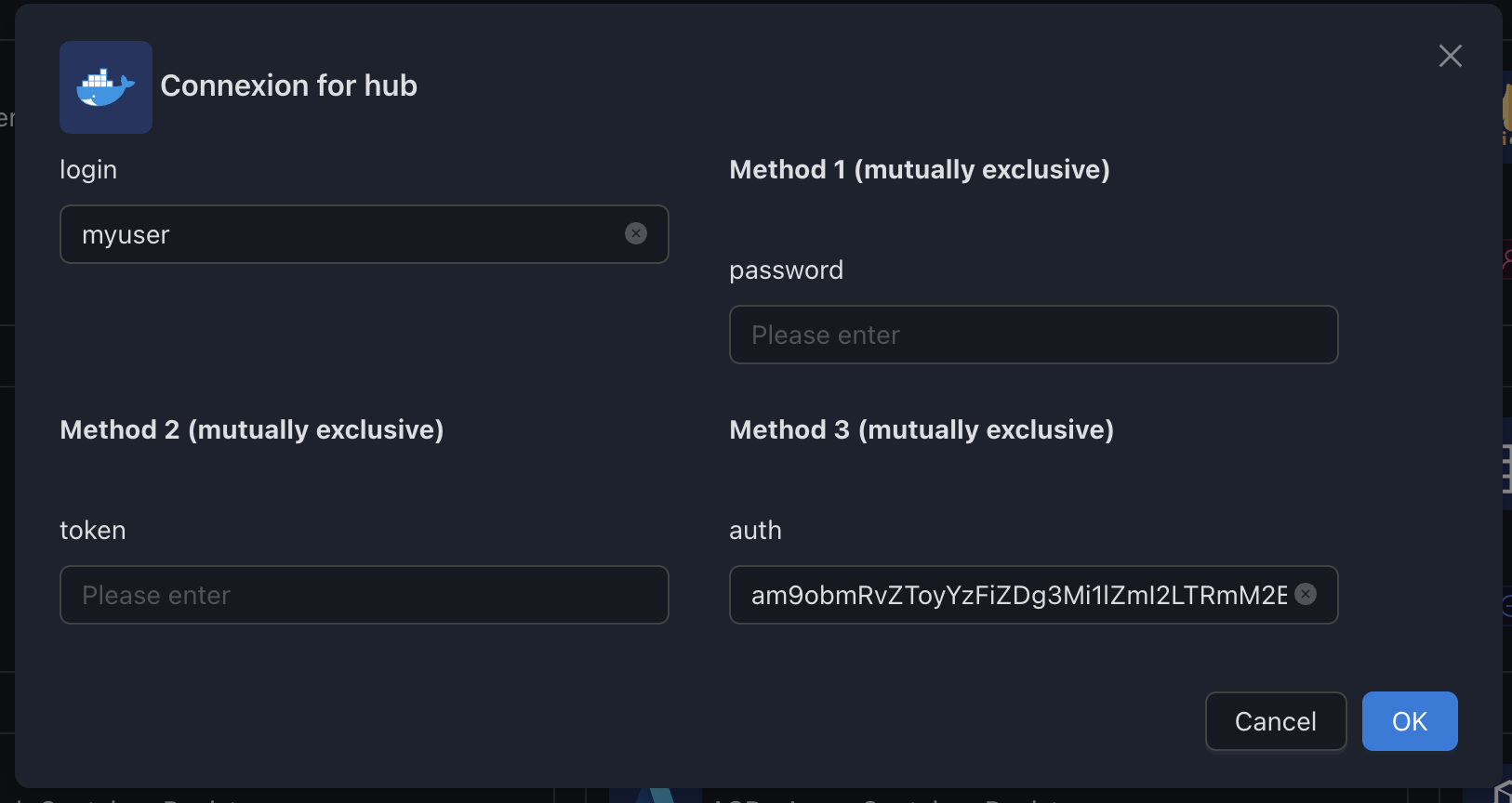
HUB (Docker Hub including private repositories)
The hub registry lets you configure Docker Hub integration.
Currently, the supported credentials are:
- Docker Hub auth + Docker Hub Access Token
- Docker Base64 credentials (like in .docker/config.json)
- Docker Hub auth + Docker Hub password (not recommended)
!> By default, if you don't configure any registries, SSM will configure a default one with anonymous access.
Don't forget to configure authentication if you're using Docker Hub Private Repositories.
Variables
| Env var | Required | Description | Supported values | Default value when missing |
|---|---|---|---|---|
login | ⚪ | A valid Docker Hub Login | token must be defined | |
password | ⚪ | A valid Docker Hub Token | login must be defined | |
token | ⚪ | A valid Docker Hub Token (deprecated; replaced by password) | login must be defined | |
auth | ⚪ | A valid Docker Hub Base64 Auth String | login/token must not be defined |
Examples

Configure Authentication using Login/Token
1. Login to your Docker Hub Account
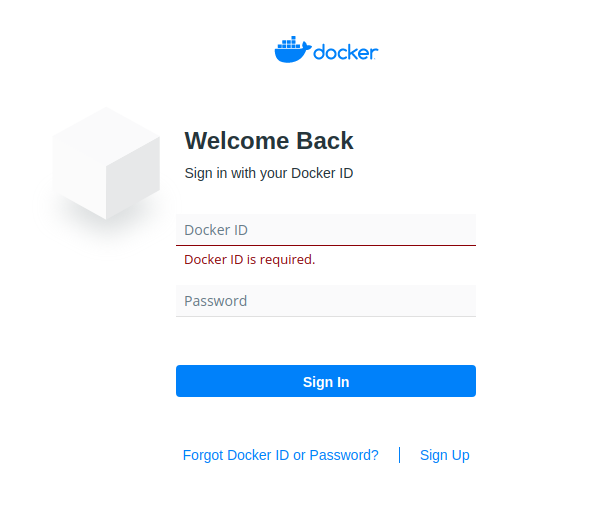
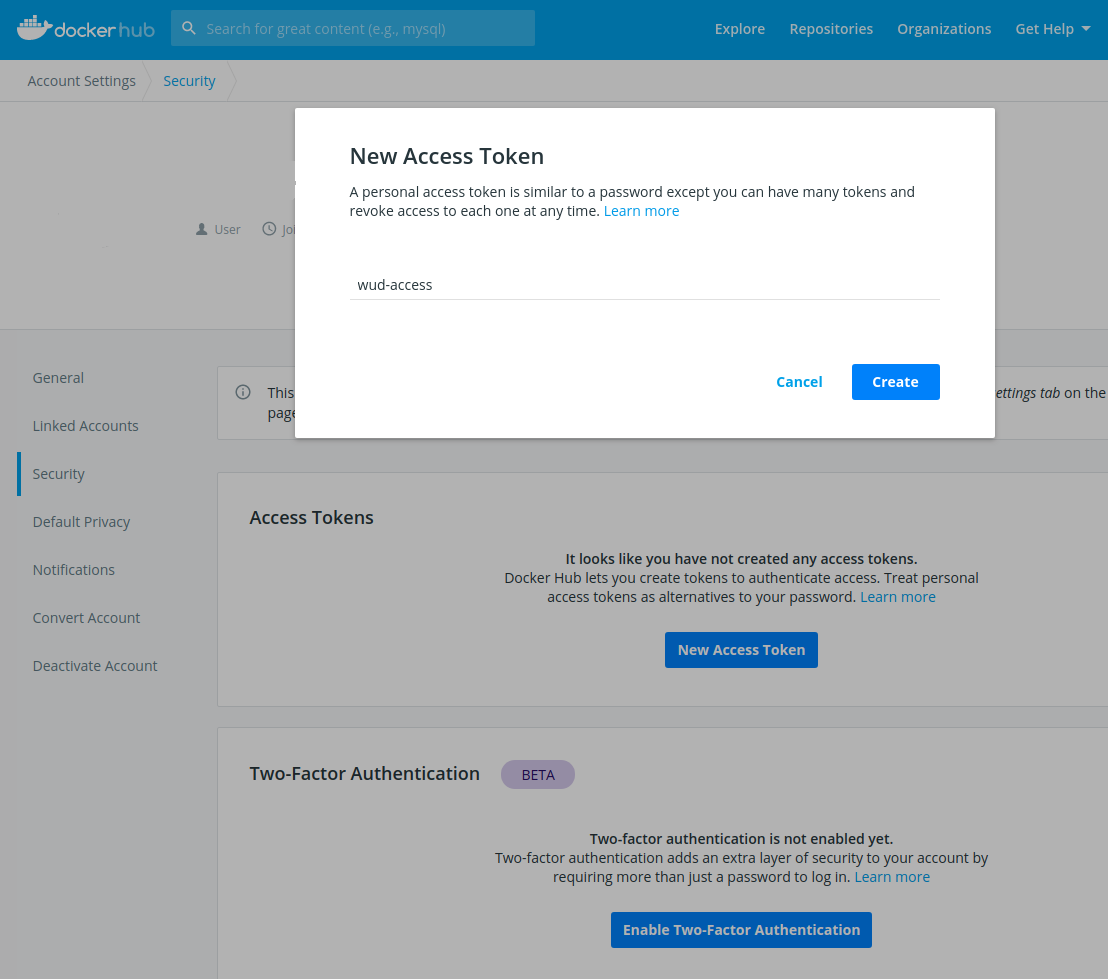
2. Go to your Security Settings
- Create a new Access Token
- Copy it and use it as the
tokenvalue
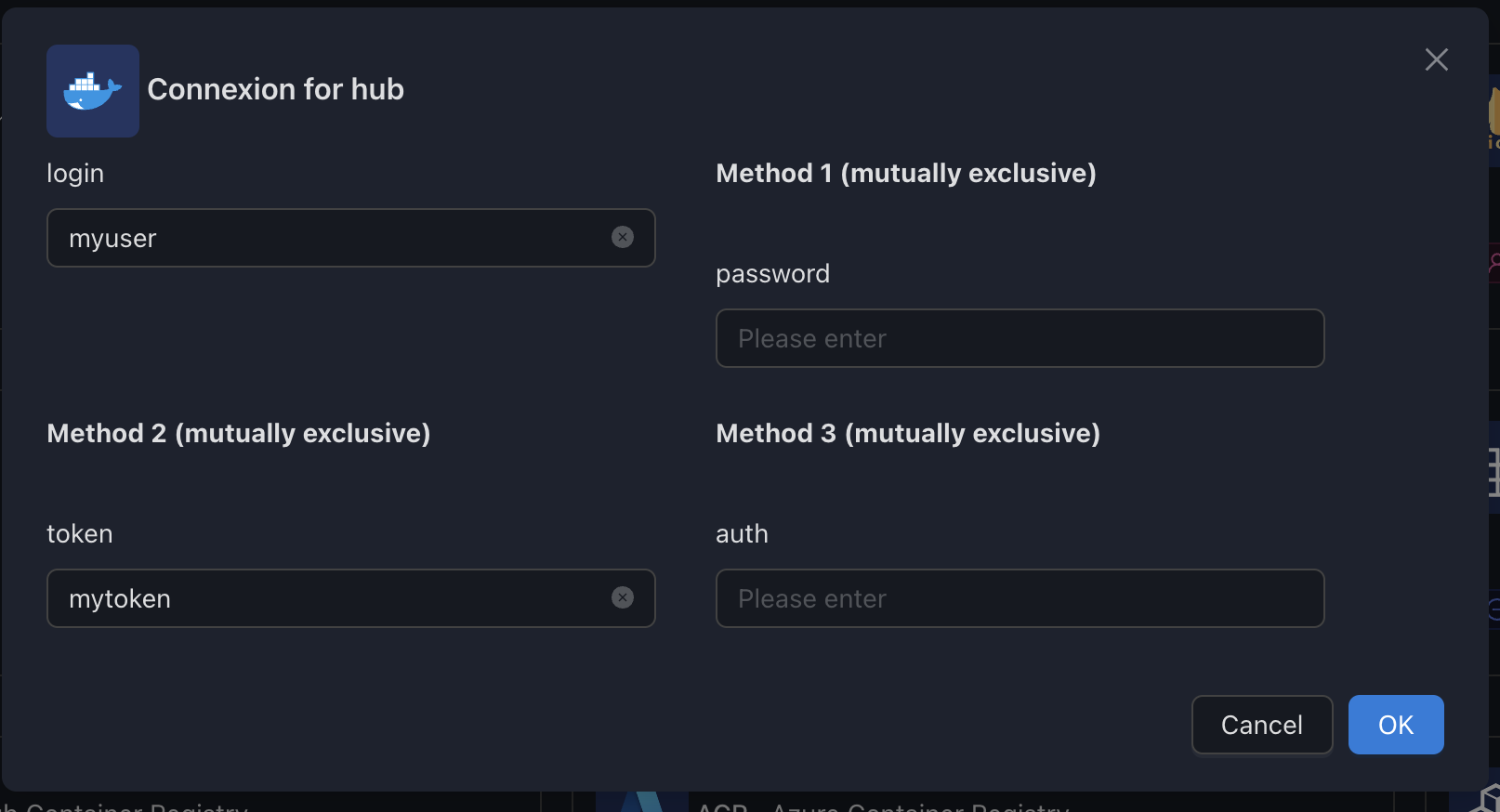
Configure Authentication using Base64 encoded credentials
1. Create an Access Token
See above "Configure Authentication using Login/Token"
2. Encode with Base64
Concatenate $auth:$password and encode with Base64.
For example,
- if your auth is
johndoe - and your password is
2c1bd872-efb6-4f3a-81aa-724518a0a592 - the resulting encoded string would be
am9obmRvZToyYzFiZDg3Mi1lZmI2LTRmM2EtODFhYS03MjQ1MThhMGE1OTI=
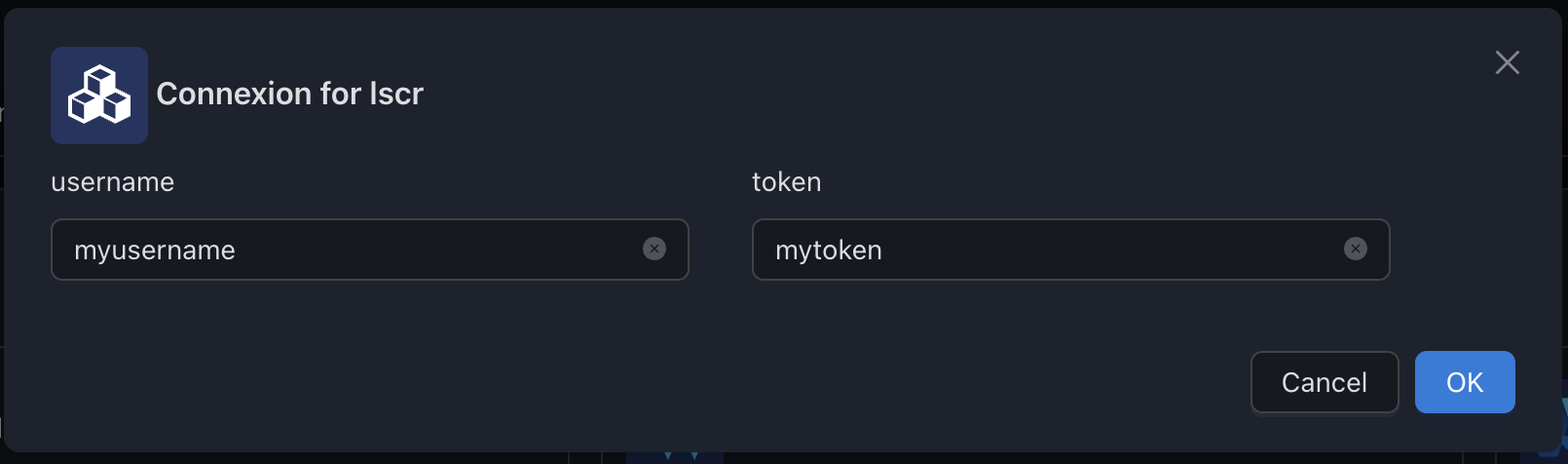
LSCR (LinuxServer Container Registry)
The lscr registry lets you configure LSCR integration.
Variables
| Env var | Required | Description | Supported values | Default value when missing |
|---|---|---|---|---|
username | 🔴 | GitHub username | ||
token | 🔴 | GitHub token | GitHub password or GitHub Personal Token |
Examples
How to create a GitHub Personal Token
Go to your GitHub settings and open the Personal Access Token tab
Click on Generate new token
Choose an expiration time & appropriate scopes (read:packages is only needed for SSM) and generate. 
Copy the token & use it as the token value

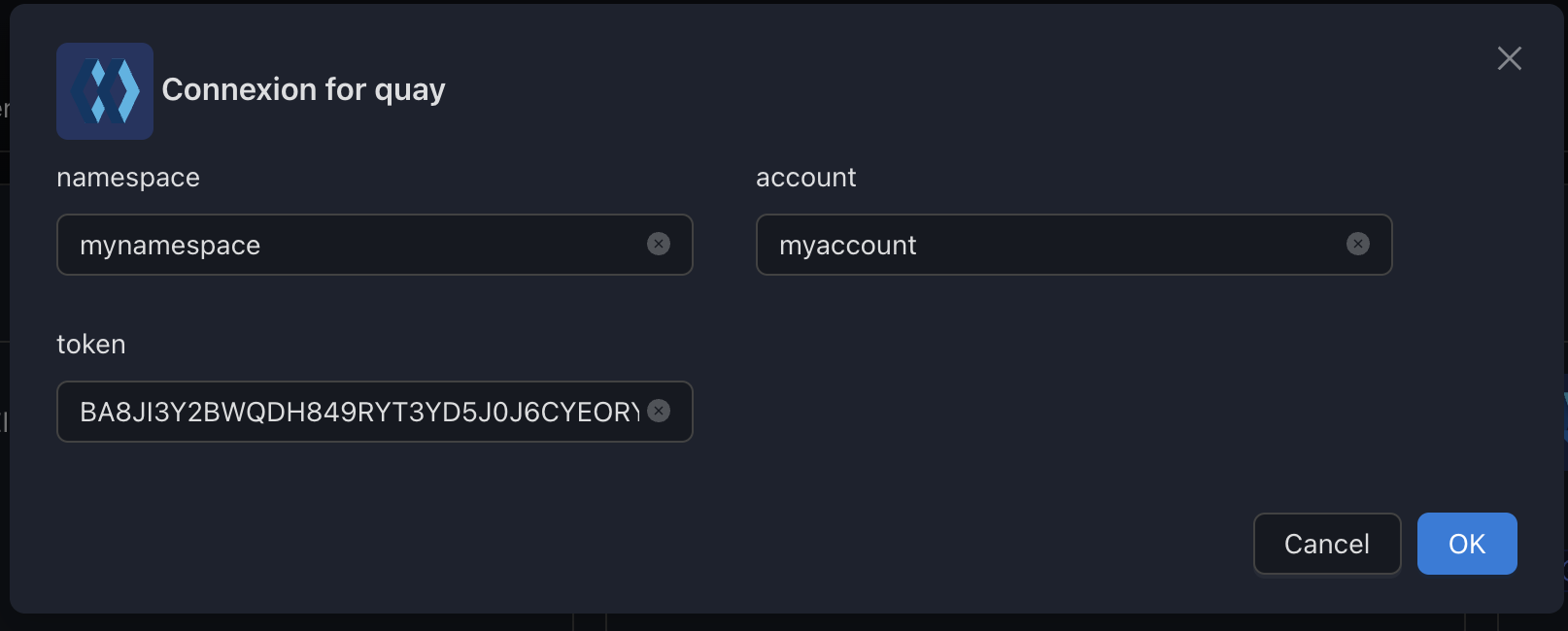
Quay
The quay registry lets you configure Quay integration.
Variables
| Env var | Required | Description | Supported values | Default value when missing |
|---|---|---|---|---|
namespace | ⚪ | Quay namespace | ||
account | ⚪ | Quay account | ||
token | ⚪ | Quay token |
Examples
Configure to access private images (credentials needed)
How to create a Quay.io robot account
Go to your Quay.io settings and open the Robot Accounts tab
Click on Create Robot Account
Choose a name & create it 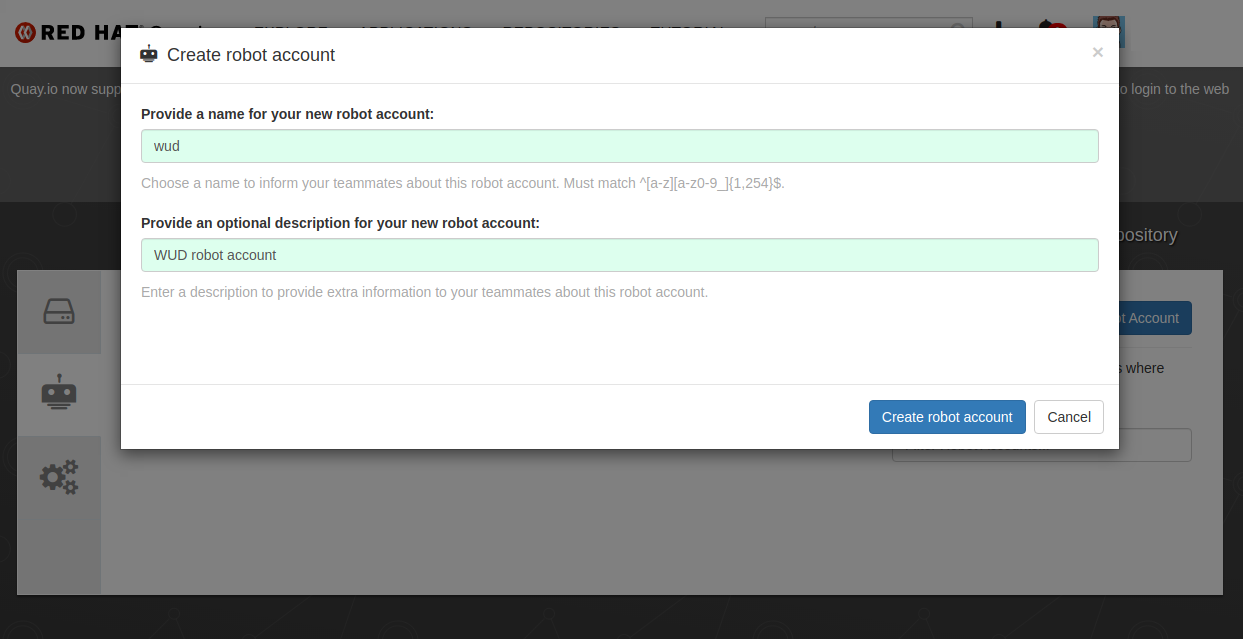
Copy the part before the + sign and set it as the namespace env var
Copy the part after the + sign and set it as the account env var
Copy the token value and set it as the token env var

Deleting a registry
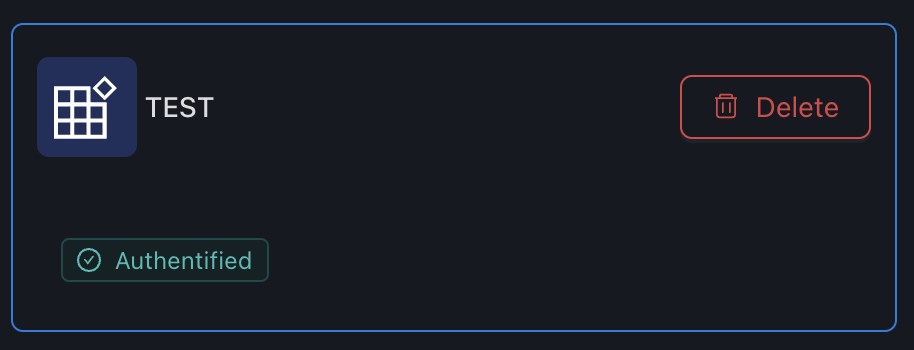
Deleting a custom registry
To delete a custom registry, simply click on "Delete" on the tile of your custom registry 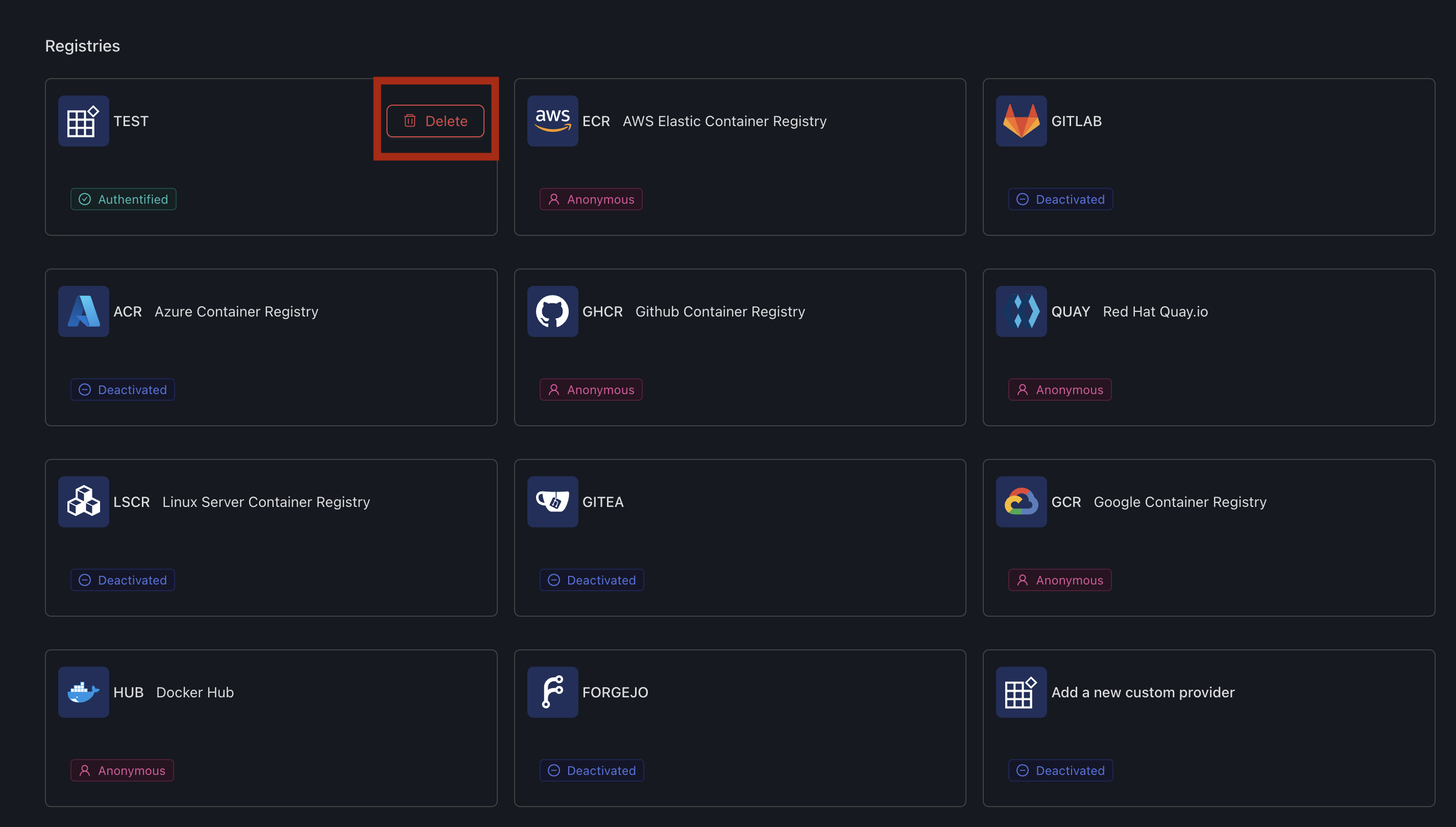
Resetting a default registry
To reset a default registry, simply click on "Reset" on the tile of your custom registry